STRENGTHS
INFORMATION SECURITY
abox ECM offers very powerful features that guarantee the security of the information and the certification of its authenticity and validity vis-à-vis third parties. These are some of the functionalities that guarantee the safety of abox ECM.
A vulnerability is a failure or weakness in system security procedures, design or implementation that may lead to a violation of the system security policy or, in other words, allow hackers unauthorized access to computer resources.
The vulnerability testing dedepends on two essential tests: Vulnerability Diagnosis and Penetration Testing. Both techniques differ in the effort involved and the tasks required in each. However, it is recommended to combine both techniques for a complete and serious analysis.
To review methodologies of safe development of applications it is recommended to evaluate BSSIMM – The Building Security In Maturity Model, Security Development Lifecycle and/or Software Assurance Maturity Model.
abox ECM has passed the vulnerability tests to which it has been subjected in several of its main implementations, in public and private sector clients.
abox ECM works under protocol HTTPS without appreciable loss of functionality or performance. Only one certificate is required SSL that allows data encryption between the server and the clients.
abox ECM can store in encrypted form the images and office files managed by the application, which is done for efficiency reasons outside the relational database.
The passwords must be secure and contain a variety of characters (uppercase, lowercase, symbols and numbers), a minimum configurable length, the possibility of programming its deactivation, the ability for each user to change it, among others.
A secure password reminder should be provided, such as sending new keys to the user’s email address. abox ECM controls a maximum connection time to prevent the user’s session from remaining after the user is no longer active in the application.
abox ECM has, among others, a register of authentications (logins y logouts) to control access to the platform.
abox ECM has the option of integrating users with the Active Directory to centralize passwords.
In abox ECM the information is stored in “contents” and organized according to a classification scheme that includes multiple levels such as dependencies, trays, series, subseries, files, etc.
The contents can be very varied in nature:
- Websites, modules, menu entries and web pages.
- Document clusters, such as files or content trays.
- Documents (cards that combine images, files and metadata).
- Metadata (grouped by schemas).
- Archives or files (which are linked to the previous contents).
- News, announcements, alerts, etc.
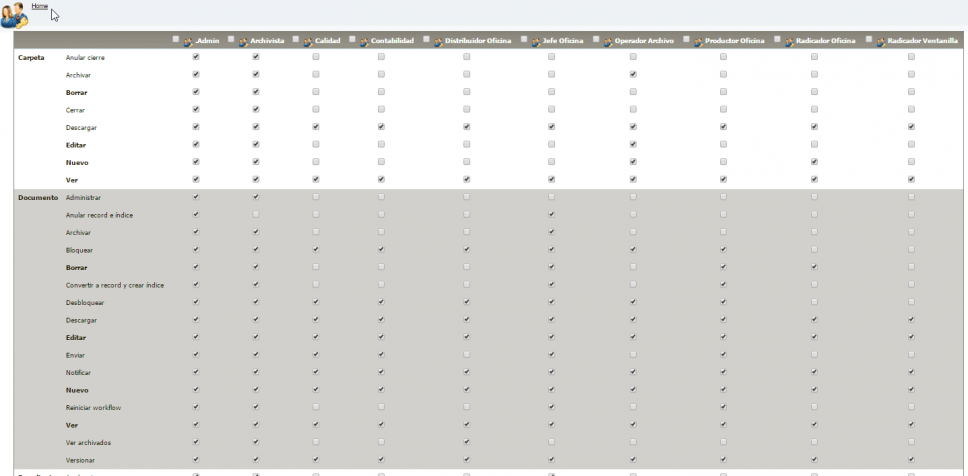
The abox ECM system implements a security policy very powerful, consisting of several steps:
- Define user roles, attending to the obligations, capacities and privileges of software management.
- Define the corporate organisation chart, on which the rights of access and consultation of the information depend.
- Assign action permissions to each of the entities managed by the software, by user roles.
- Associate users with appropriate dependencies and roles, which will determine their credentials for consulting and updating information.
- Assign websites, modules and menu entries by roles and/or user dependencies.
- Assign access and editing permissions to trays, organized by dependencies.
- Assign query and editing permissions to the metadata handled in the tool.
The access permissions are configured by default in the trays that correspond to each dependency and are inherited automatically. It is possible to assign individual licences to a single file or a single document, or configure permissions for classes of files or documents. The control of action permissions is done by modules, with dozens of entities where you can specify the permission by role in a very detailed way.
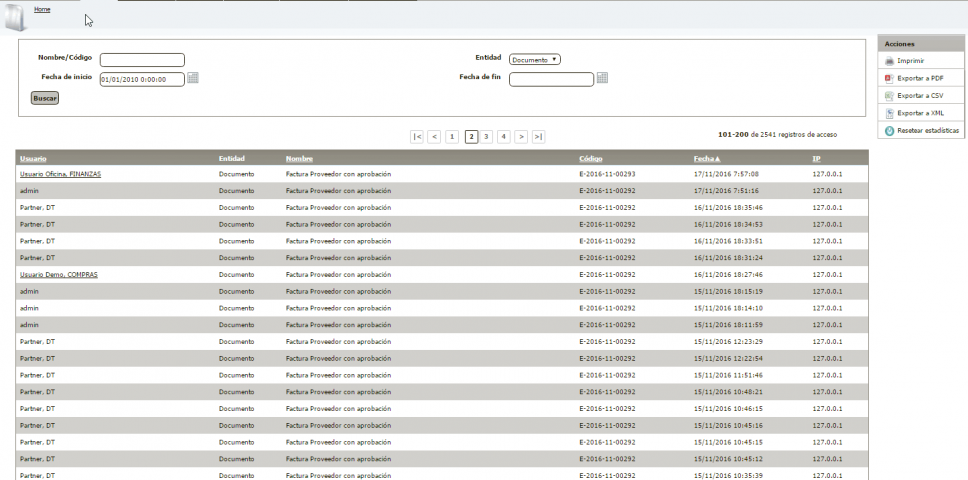
abox ECM register the activity of all its users, including capturers that automatically upload documents to the system.
The main variables controlled by the system are:
- Logs of errors or system intrusions. Here you can work with access reporters and errors of the operating system or framework itself, some of them “open-source”, very useful to alert administrators about incidents in the application (example: ELMAH system).
- Audit logs. The system logs critical actions performed on users or system contents, including details of actions performed, modifications made, date/time, access IP, etc.
- System Authentication Logs. The system logs access logins and logouts, as well as frustrated attempts.
- Logs of notifications. The system registers notifications sent by e-mail, either at the request of users or automatically sent by the system (e.g. alerts).
- Access Statistics. The application registers access statistics to the main contents managed by the application, i.e. files and documents.
- Download statistics. The application knows if a content was downloaded by a certain user.
Permanent control measures are not always required. There are certain functionalities that can help to preserve the confidentiality of documents also on a provisional basis.
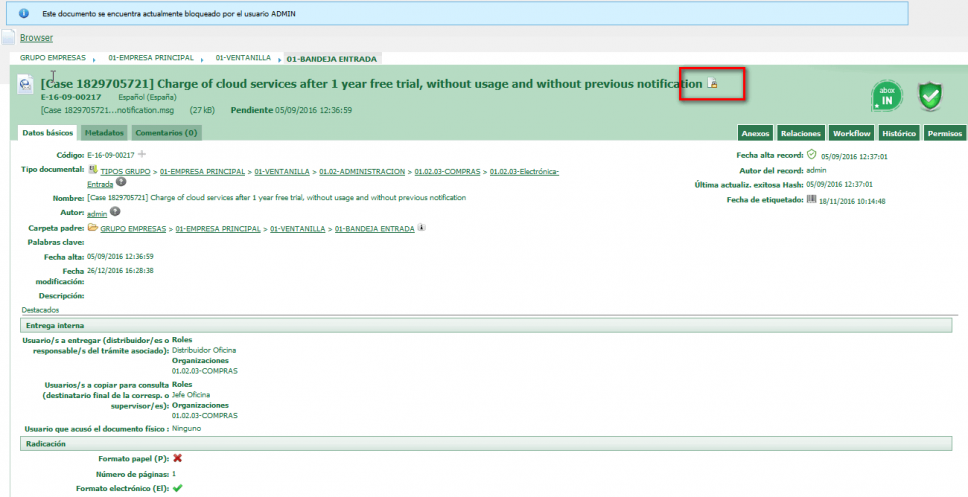
One option offered by abox ECM is the blocking of attachments, in order to prevent any user from viewing or downloading a document (its main image or attachment), as long as the document remains blocked.
Another option is to declare a document as confidential, which will prevent it from being found and consulted by other users, except for those roles of maximum responsibility that are determined in the software parameterization phase.
The closures of a tray or a file ensure that the contents stored within those trays or files are not modified. The closure prevents any alteration, inclusion or deletion of contents.
Once a file has been closed, only persons with a special administrative permit may reopen it. The reopening will be recorded in the audit trail of the file itself.
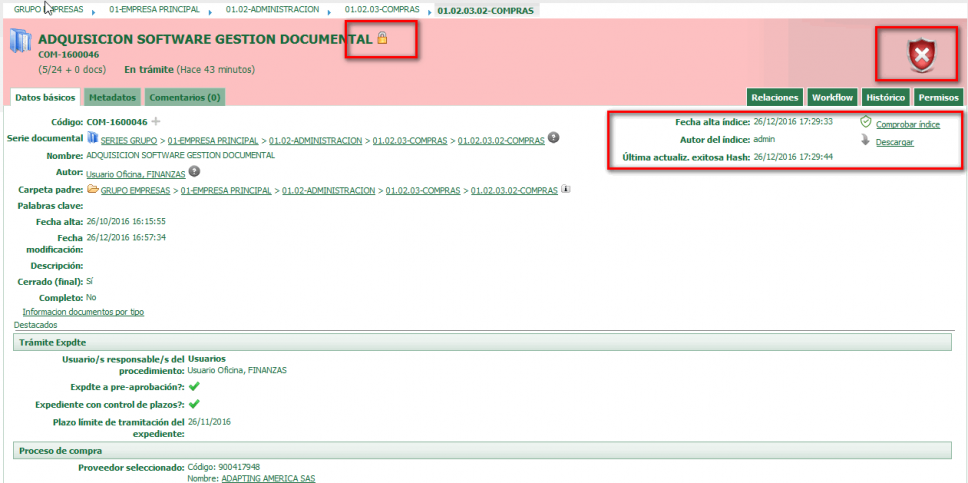
There is an option of maximum security that is the certified closure with index. The index allows to detect changes in the composition of the tray or file by means of a secure fingerprint or “hash”. Additionally, it is possible to download the index in order to inventory the contents of the tray or file.
The index represents a higher level of security for the closure of trays and files, although it is so sensitive that the slightest change in the contents will make it invalid and the container will be marked in red.
For the fulfillment of the archival standards it is important to store documents in standard formats, which are not dependent on a specific manufacturer (such as Microsoft), and which are guaranteed to be supported and preserved over the long term.
The ISO-19005 standard proposes the format PDF/A as a standard for long-term document preservation. This standard does not define a strategy for storage, but rather identifies a “pattern” for electronic documents to ensure that they can be reproduced accurately in the future.
A key element in achieving this goal is the requirement for PDF/A documents to be 100% self-contained. All the information needed to display the document consistently will be present in the archive. This includes, among other things, the content itself (text, images and vector graphics), the fonts used, and color information.
abox ECM allows conversion to PDF/A 1a and 1b formats at any point in the document flow (e.g. when the file is sent to the archive), making it possible at that time to replace the main attachment with the PDF/A equivalent, or to supplement the actual attachment (e.g. in Word) with a secondary attachment that is its PDF/A equivalent.






